Introduction:
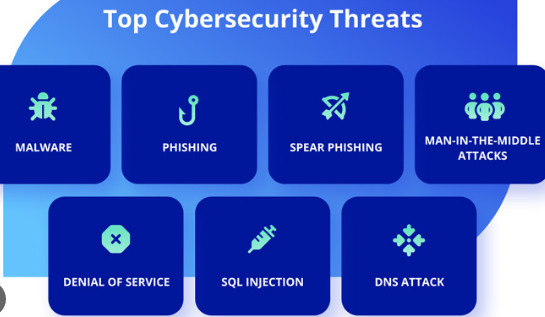
In our interconnected world, where technology permeates every aspect of our lives, ensuring robust cybersecurity measures has become more critical than ever. Cyber threats continue to evolve, with hackers employing increasingly sophisticated techniques to exploit vulnerabilities. To protect our digital frontiers, it is imperative to understand the features of cybersecurity and implement comprehensive strategies to safeguard our sensitive information. In this article, we will delve into the key features of cybersecurity and explore their significance in defending against cyber threats.
cybersecurity image - Risk Assessment and Management: A fundamental aspect of cybersecurity is conducting a thorough risk assessment. Organizations and individuals must identify potential vulnerabilities, evaluate the likelihood of exploitation, and assess the potential impact of successful cyberattacks. By understanding these risks, appropriate security measures can be implemented, and resources can be allocated effectively to mitigate potential threats.
- Network Security: Network security serves as a vital defense mechanism against cyber threats. It involves establishing secure network configurations and implementing firewalls, intrusion detection systems, and virtual private networks (VPNs) to protect data transmitted over networks. Encryption techniques are used to ensure data confidentiality, integrity, and authenticity, preventing unauthorized access and tampering.
- Identity and Access Management: Securing user identities and managing access privileges is crucial to prevent unauthorized access to sensitive data. Implementing robust authentication mechanisms, such as multifactor authentication (MFA) and biometric verification, ensures that only authorized individuals can access critical resources. Access controls, including role-based access controls (RBAC), limit privileges based on job roles, further enhancing security.
- Incident Response and Recovery: Despite preventative measures, cyber incidents can occur. A well-defined incident response plan helps organizations respond swiftly and effectively to security breaches. This involves identifying the nature and scope of the incident, containing the damage, restoring systems, and preserving evidence for forensic analysis. Regularly testing and updating incident response plans is crucial to ensure their effectiveness in addressing evolving cyber threats.
- Threat Intelligence and Monitoring: To stay one step ahead of cybercriminals, organizations need to actively monitor their networks for suspicious activities and indicators of compromise. Employing advanced threat intelligence solutions allows for the proactive identification of emerging threats and vulnerabilities. Continuous monitoring of systems and networks helps detect anomalies and potential breaches, enabling timely responses and mitigating potential damage.
- Security Awareness and Training: Human error remains a significant factor in cybersecurity breaches. Comprehensive security awareness programs educate employees and individuals about safe online practices, social engineering threats, and the importance of data privacy. Regular training sessions and simulated phishing exercises reinforce security best practices and foster a security-conscious culture within organizations.
- Data Protection and Privacy: Data is a valuable asset, and safeguarding it is crucial for maintaining trust and complying with regulations. Encryption, data classification, and data loss prevention measures protect sensitive information from unauthorized access, both at rest and in transit. Compliance with privacy regulations, such as the General Data Protection Regulation (GDPR), ensures that personal data is handled securely and transparently.

Conclusion:
Cybersecurity is an ongoing battle that requires a multi-faceted approach to protect against ever-evolving threats. By incorporating robust risk assessment and management, network security, identity, and access management, incident response and recovery, threat intelligence and monitoring, security awareness and training, and data protection and privacy measures, individuals and organizations can strengthen their defenses. In an era where digital connectivity is pervasive, a proactive and comprehensive cybersecurity strategy is essential to safeguard our digital frontiers and protect sensitive information from cybercriminals.
